Common Mistakes You Can Avoid While Using Your Computer
Sunday, April 13th, 2014Like installing free software that is suspicious, backing up data…
Install unwanted Free Softwares and Offers that are suspicious:
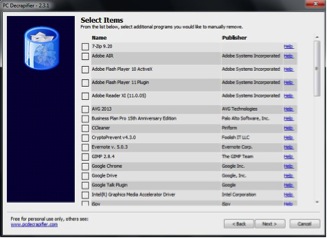
Some pre-installed applications are bad and some you may have no use and others may even turn out to be sub-standard and slow down your computer. Checking your PC for each item you didn’t ask for will probably take you a while. For this, PC Decrapifier application helps you identify unwanted junk. Once you can run the wizard it shows you a checklist with recommendations and tick the programs, icons and start-up items that don’t want and then click the Next button as shown in the screenshot below.
Everyone loves free things. Free software is often ad-supported and in many cases the installer comes bundled with additional products or ad-ware, which can slow down your computer. So, anytime you download a free Windows application, you must do a custom install. And several other kinds of software that are alternatively offered or forced when installing free software and these can include several different types of software.
And another type of unwanted software are browsers, it could be easily modified and include unwanted piece of functionality that does something you don’t want, like monitor your activity or steal personal information. If you want a new browser, it is much safer to go directly to the source, and if you decided you preferred Firefox or Chrome to Internet Explorer to accept what comes bundled with other software.
Also, several varieties of trial software are also often offered. And these include games which may require an additional purchase to continue playing, or offers of security solutions. This latter option can be particularly risky to install, especially if you already have other security in place. Having two security solutions in place, with the same kind of functionality being offered, can lead to conflicts and computer crashes. Just like with browsers, it is better to make an informed choice and download and install security solutions from their official webpage, instead of using what comes bundled with other software.
Then finally, some software may ask or require you to sign your email up for spam, change your homepage to their website, or even buy into other promotions in order to enjoy the product for free.
Backing up data:
There are many reasons for data loss and some of the most common are: accidental deletion, hard disk damage or failure, viruses, power disruption and improper shutdown.
Also, please avoid the following common mistakes for backing up data.
o Save your work
o Close applications
o Configure new file types
o Update backup sets
o Rescue disk
o Database exports
o Check backup media
o Check log files
o Verify recent backup data
o Store backup media offsite during absence
o Critical data should be backed up 2 ways
o Run Error Check on the C: drive
Too Much Disk Defragmentation
Most people don’t need to defragment their hard disk manually. And you should only defragment your hard drive if it is 5-10% fragmented.
Not Restarting the Computer
Rebooting is considered a cure-all of sorts that fixes a ton of problems. So try to reboot and see if that solves the problem.
Viruses, Trojans, and Adware
Another one of those problems that can be a risk with any new software download. Having solid anti-virus software on your computer is a must for this.