What is GNU and what are the benefits of using it?
Thursday, April 3rd, 2014Basic introduction
GNU is a Unix-like computer operating system developed by the GNU Project. It is composed wholly of free software. It is based on the GNU Hurd kernel and is intended to be a “complete Unix-compatible software system”. GNU is a recursive acronym for “GNU’s Not Unix!” chosen because GNU’s design is Unix-like, but differs from UNIX by being free software and containing no UNIX code.
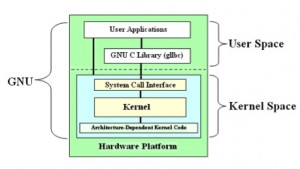
Basic architecture of GNU OS
Advantages and disadvantages
Advantages of GNU:
o Low Cost
o Open Source software packages
o Stable
o Performance
o Network friendliness
o Compatibility
o Configurability
o Multitasking
o Security
o Ever improving without adding cost to the end user
Disadvantages of GNU:
o Learning curve is higher for people exposed only to MS Windows
o It was initially designed by programmers for programmers, so for normal users it’s difficult to grasp at the beginning
o Not all MS Windows application equivalents present in Linux
o Administration of Linux systems is tough for beginners
o Not all hardware are compatible, especially peripherals, whose drivers may not exist Comparison with Windows
Comparison with Windows
This section compares the Windows and GNU architectures.
Kernels and APIs
o In GNU, the API functions are called system calls. And Windows has an API for programming calls to the executive.
o Windows has an API for programming calls to the executive. In addition to this, each subsystem provides a higher-level API.
Kernel Objects and Handles
o In UNIX, the kernel object can be created using the system calls and it returns an unsigned integer. There is no exact equivalent of handles in UNIX.
o In Windows, Windows APIs are used to create the kernel object and it returns a Windows-specific data type called HANDLE.
Hardware Drivers
o In GNU, there are several different ways to manage drivers.
o In Windows, the Windows driver model provides a platform for developing drivers for industry-standard hardware devices attached to a Windows-based system.
Process Management
o Both Windows and GNU operating systems support processes and threads.
o The sections provide more details on process management in both GNU and Windows are Multitasking, Multiple users, Multithreading & Process hierarchy’.
Daemons and Services
o In GNU, a daemon is a process that the system starts to provide a service to other applications.
o A Windows service is the equivalent of a GNU daemon. It is a process that provides one or more facilities to client processes.
Virtual Memory Management
o Both GNU and Windows use virtual memory to extend the memory available to an application beyond the actual physical memory installed on the computer.
Security
o GNU uses a simple security model.
o Windows uses a unified security model that protects all objects from unauthorized access.
Networking
o The primary networking protocol for GNU and Windows is TCP/IP.
User Interfaces
o GNU supports the graphical user interface using the X Windows system.
o The Windows user interface was designed to take advantage of advancements in the graphics capabilities of computers.
System Configuration
o GNU users generally configure a system by editing the configuration files with any of the available text editors.
o Windows has GUI tools for configuring the system.
DLLs and Shared Libraries
o Windows and UNIX both have a facility that allows the application developer to put common functionality in a separate code module.